ISAC Platform Web 20.10
Change in Default Login Flow
If clients do not need SSO capabilities, they can use the default Zinier login.
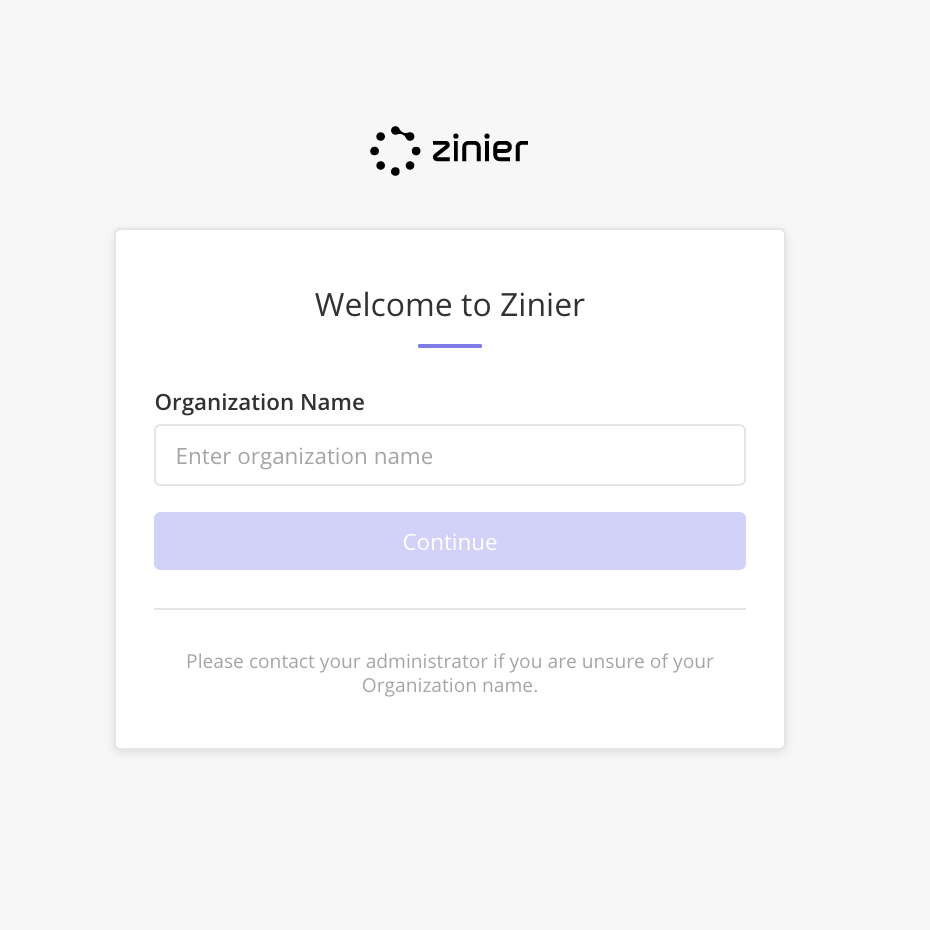
From ISAC 20.10 across web and mobile, the user login flow:
Enter the Org Name.
To change their organization, the user can click Login to a different organization. He will then be redirected back to the page to enter the Org Name.
If a user enters an incorrect org name, the user will receive an error message and not be allowed to log in.
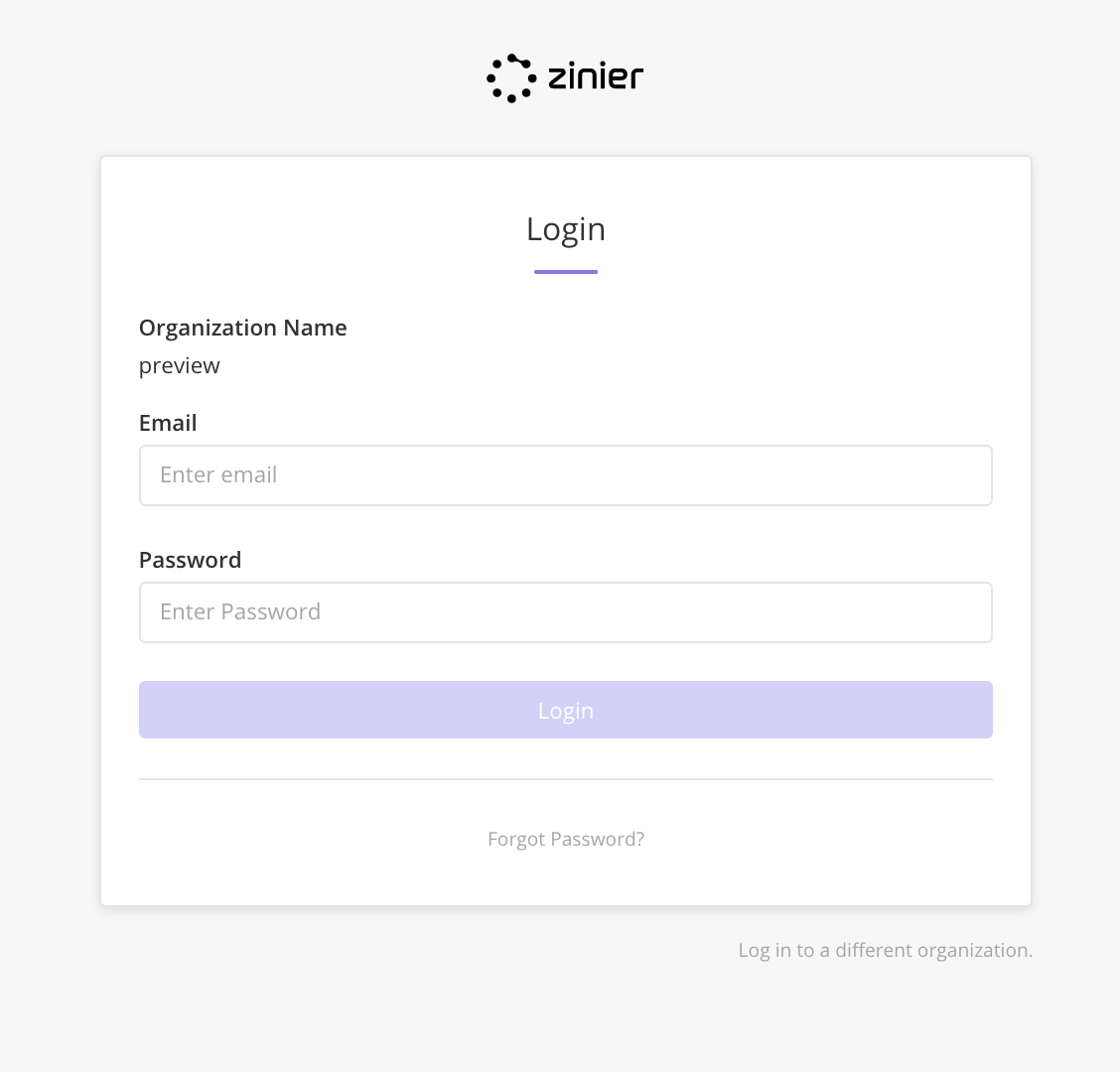
Enter the email and password.
On Logout, the user is redirected to enter the Org Name again.
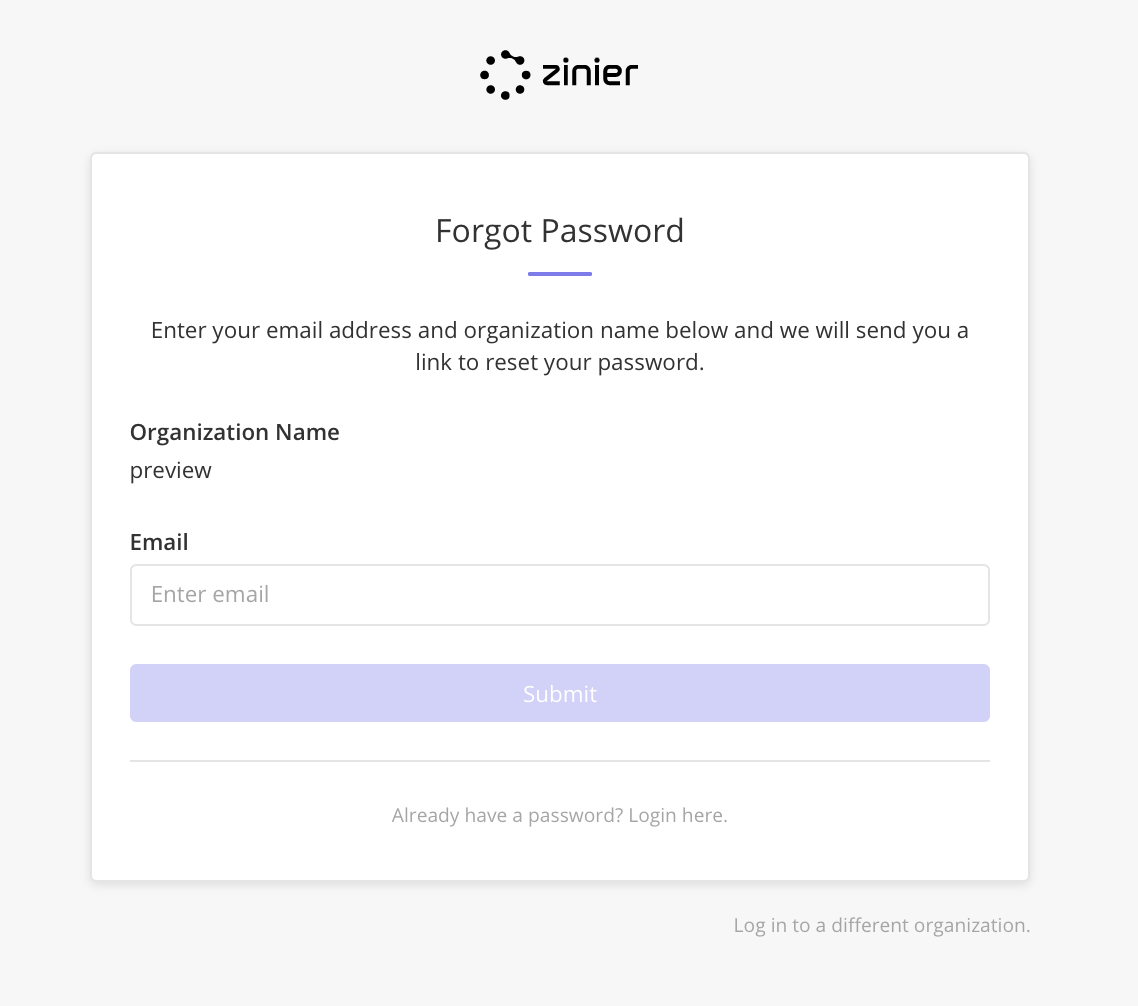
The Forget Password flow remains the same.
Login via Auth0
Zinier now supports Auth0 integration.
For clients that use SSO access to integrated apps like DOMO inside of Zinier, they can opt to Login via Auth0 as IDP.
To use DOMO Integration, users previously must log in separately into DOMO to see DOMO widgets inside the Zinier web app. With this release, users now do not need to sign individually if DOMO and Zinier both use Auth0 as IDP.
If a new or existing customer needs Auth0 enabled for any of their orgs, a production instance must be configured in Auth0.
For production orgs, please contact DevOps to set up.
Using Auth0 to login to Zinier
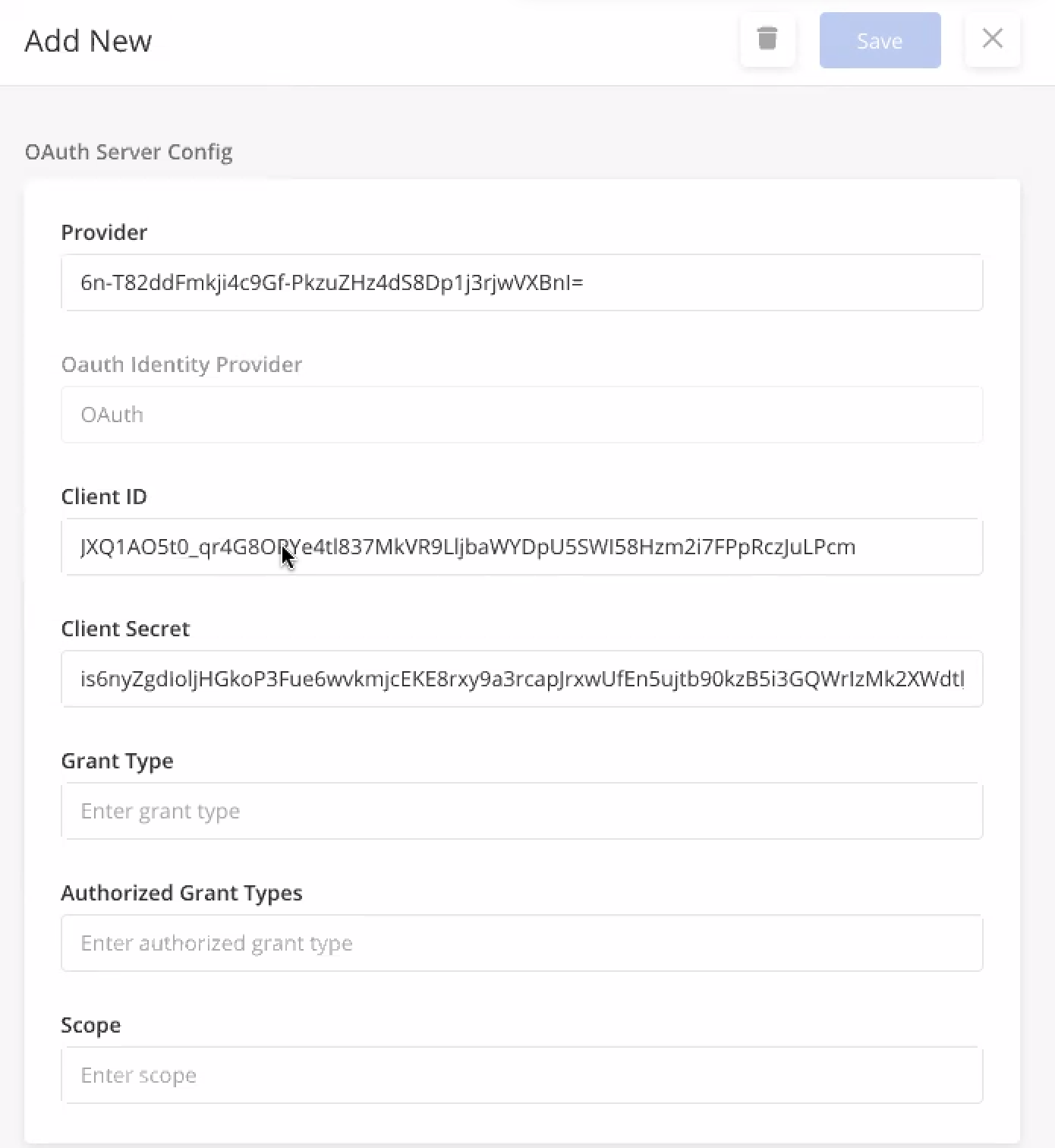
DevOps set up the production instance in Auth0 and generate the OAuth Server Config for the client.
In the org, Solution Admins must add the following entity configs/;
Config Key | Config Scope | Config Value | Value Type |
|---|---|---|---|
authProvider | login | ZINIER | string |
authType | login | OAuth | string |
In the Org, Solution Admin must configure the OAuth Server Config. This includes the Client ID and Secret Key generated by DevOps.
Login via Auth0
These steps show when Auth0 is enabled for an org.
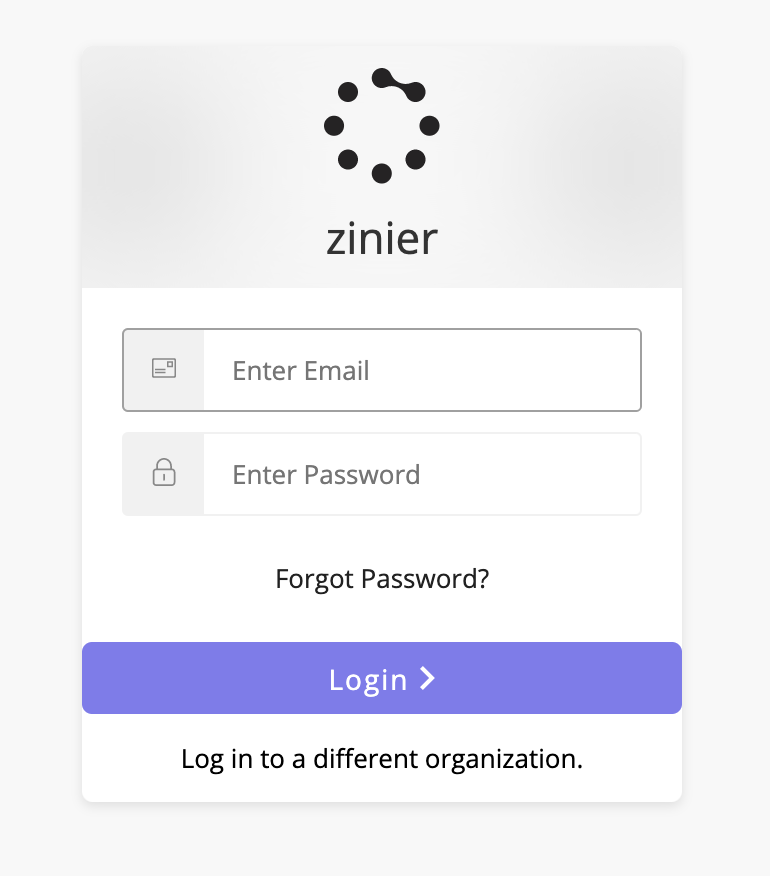
After entering the org name, the user is redirected to the Auth0 login page.
On the Auth0 login page, user can:
Enter email and password credentials to login into Zinier.
Click Forgot Password if the user forgets their password and will be redirected to the Forgot Password page. The flow remains unchanged.
Click Login to a different organization’ if he wants to change the organization. He will be redirected back to the page to input Org Name.
If there are any errors in login, like wrong password or email, the user will be notified via error messages in Auth0 login.
On mobile, if the user is trying to login to an Auth0 enabled org, the user is redirected to the Auth0 login on a browser in the mobile. After login, the browser will automatically redirect the user back to the Zinier Mobile app.
Login by External IDP via Auth0
This is a BETA feature with open issues.
For clients that have an existing External IDP that they use company-wide, they can opt to log into Zinier via that External IDP.
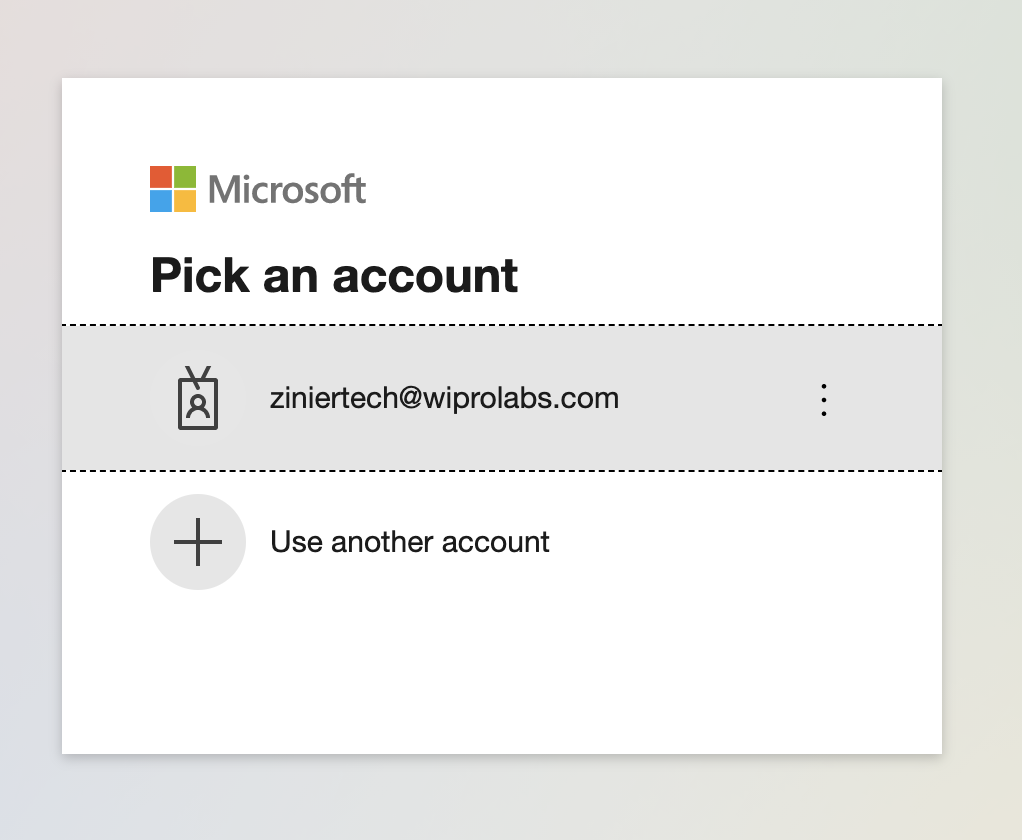
We have done this successfully for a potential client using Microsoft Azure.
Other IDPs like Okta, Google can be configured too.
For new external IDPs, Solutions must factor in Configuration testing as part of delivery.
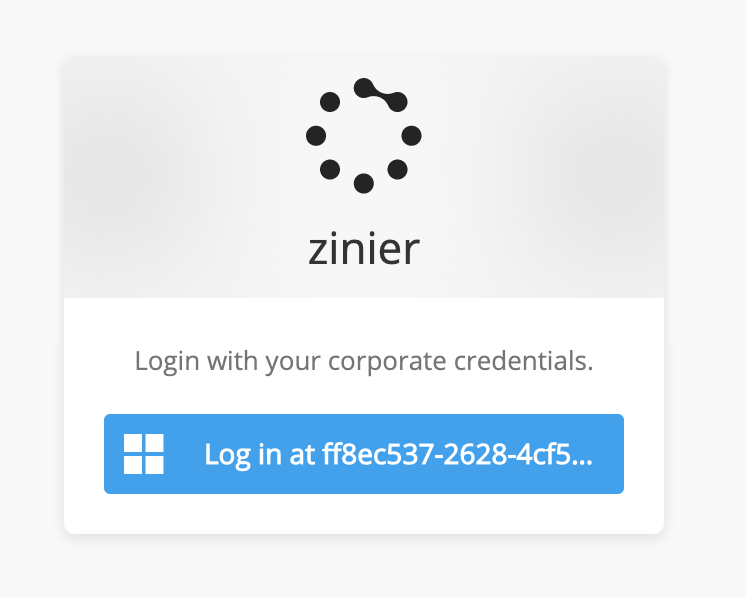
If a new or existing client wants to use their own Corporate IDP to login to Zinier via Auth0, a production instance must be configured in Auth0.
DevOps is overseeing the set-up process. Please contact DevOps to get this set up.
Set-up External IDP via Auth0
Step 1: DevOps will set up the production instance in Auth0. They will generate the OAuth Server Config for the client.
Step 2: In the org, Solution Admins must add the following entity configs
Config Key | Config Scope | Config Value | Value Type |
|---|---|---|---|
authProvider | login | NON-ZINIER | string |
authType | login | OAuth | string |
userAuthorizationWF | SSO | ssoCustomWorkflow | string |
Step 3: In the Org, Solution Admin must configure the OAuth Server Config. This includes the Client ID and Secret Key generated by DevOps.

Step 4: In the Org, Solution Admin must choose which Group is a default Group. This will be the Group assigned to new users who log in to Zinier via External IDP. Solution Admin must remember to assign web apps to that default group so that new users will be able to see something when they login
If no group is marked as default, new users who log in to Zinier via External IDP will not have any group assigned. He will see a blank white page. This is an open issue that will be fixed.
Step 5 (Optional): If the Solution Admin wants to configure the default role type to new users who login via External IDP, they can write a stateless workflow that does this. For example, in the stateless workflow, they can choose to give Solution Admin as the default role. In Org Config, the config value for userAuthorizationWF must be the name of the custom workflow they defined in this step.
If Step 5 is not set-up, the Platform will be default assign Project User role and default Group assignment to any new user who logs in with External IDP.
New user login to Zinier with External IDP via Auth0
New users can input the Org Name. This Org Name must be set-up as a Corporate-IDP enabled org through the Steps above.
User is redirected to Auth0 login page with instruction to login via Corporate IDP like Microsoft Azure
As this is a new user, the platform automatically creates and activates this account on successful login via Corporate IDP.
The platform auto-assigns this user based on role type in custom workflow set up in Step 5 above OR assign default role level of Project user if no custom workflow exists
The user is assigned to a default group based on the default group selection in Users.
If there is no group assigned as default, on login the user will encounter a blank white page. This is a known open issue and will be fixed in the next release.
If an existing user wants to login via External IDP
Existing user enters Org Name. This Org Name must be configured as a Corporate-IDP enabled org.
The user is redirected to Auth0 login page with instructions to login via Corporate IDP.
The user logs in with Corporate IDP credentials and is redirected to Zinier.
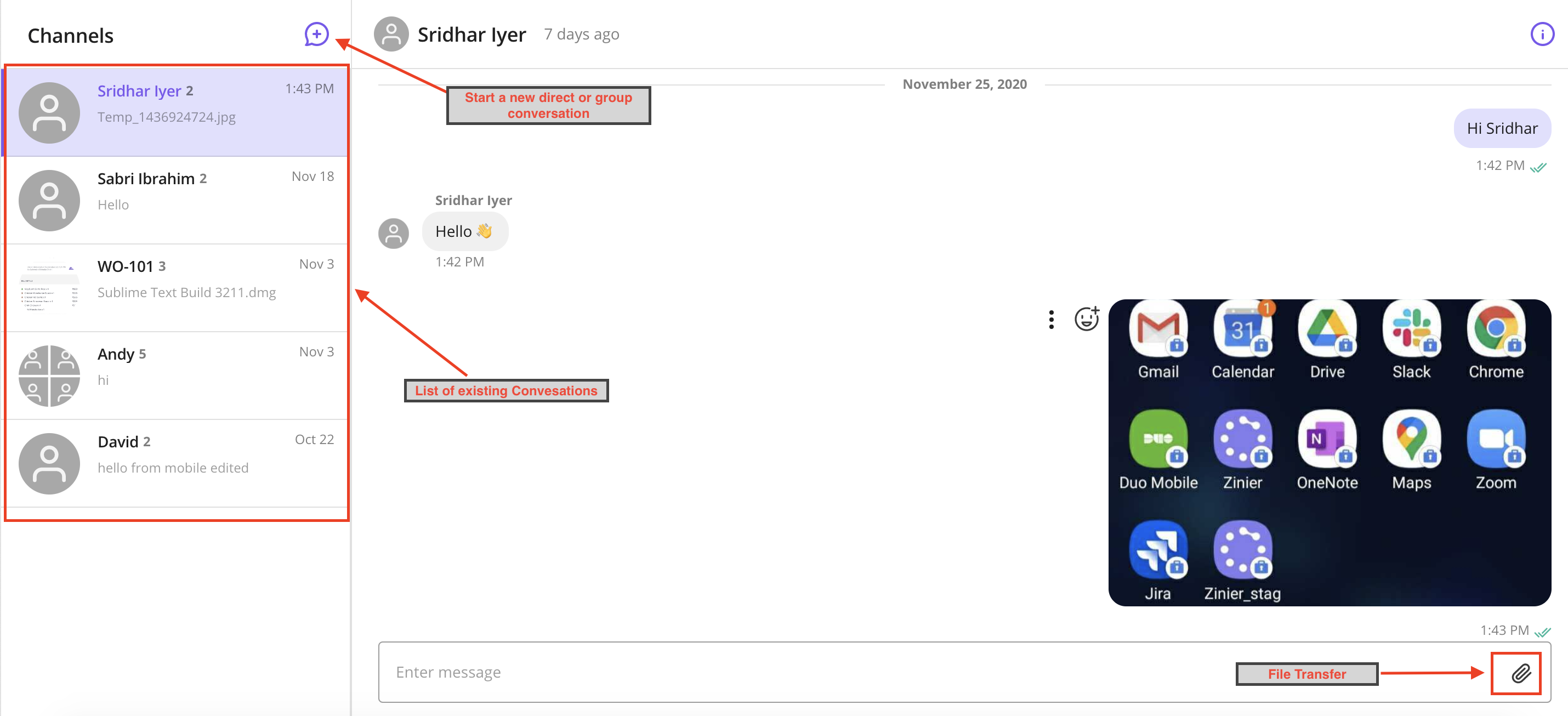
In-App Messaging V1
This is a BETA feature.
Real-time messaging can now be enabled for clients on the Zinier Platform. Users can send messages across platforms ie. Web, IOS, and Android.
Chat features include:
Messaging essentials:
Peer to Peer and group messaging
Typing indication, Delivery receipt
Message timestamp
File transfer: JPG, PDF, etc. (File size limit of 25 Mb)
Push notifications on all platforms (Web, IOS, and Mobile)
What is not available?
Localization
Audio/video call
User presence (Online, Away, etc.)
Offline delivery and Device sync (Deliver message when the sender comes back online)
How to enable messaging?
Details on enabling messaging for an Org:
Application ID to be created in the Sendbird Dashboard (Application ID and API Token is needed for Sendbird Configuration)- Raise a request to Dev Ops
Org config settings - To be added by Solution/Web Admins
- CODE
Config Key: inAppMessagingEnabled Config Scope: feature Value Type: Boolean Config Value: True Encrypted: No - CODE
Config Key: sendbirdConfiguration Config Scope: feature Value Type: JSON Config Value: {"sendBirdApiToken":<<API TOKEN>,"sendBirdApplicationId":<<0295CA9E-2B78-4BEF-8F46-F60D13CAA4EA>>}
Org key to be generated for system user - Done by Dev Ops
Details on the API for org specific key generation:
EndPoint:CODEMethod: POST URL: {{host}}/system/generateOrgKeyHeader:
CODEContent-Type: application/json loginId: {{loginId}} orgId: {{orgId}} token: {{token}}Body:
CODE{ "data": [ { "orgId": {orgId} } ] }The platform ensures that all new registrations are updated in the Chat after the messaging is enabled. Existing users can be created in Sendbird by running the batch API (To be done by the Server team)
Add Push notification token details in the Sendbird dashboard for enabling push notifications - To be done by Dev Ops Team
UI Reference:
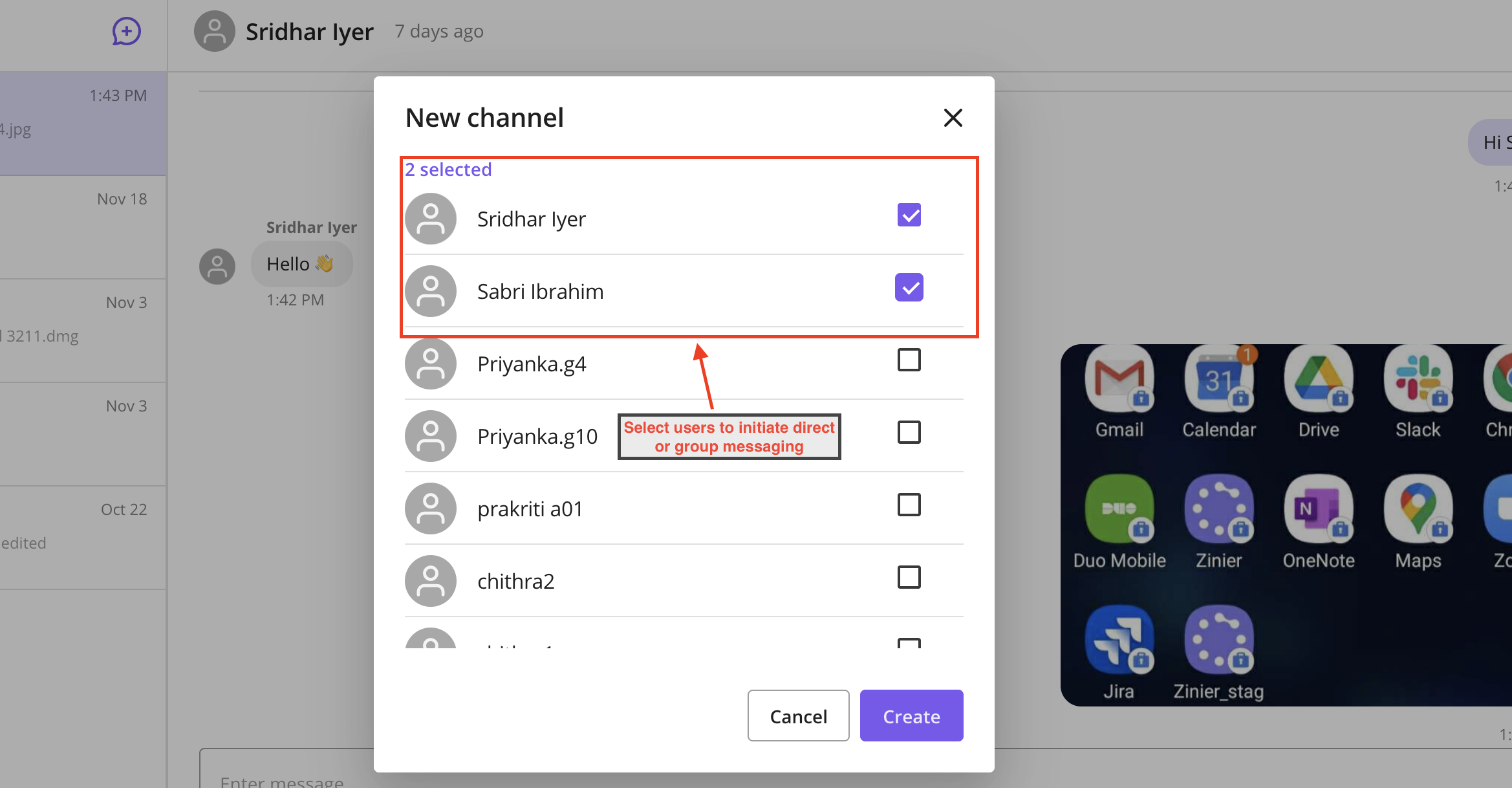
Datagrid - Sticky Headers
When users scroll on a datagrid, the headers for the data grid is now fixed and does not change its position on the scroll. During a horizontal scroll inside the grid, the header also scrolls.
The sticky headers are now available on all datagrids displayed on:
Main page
Dashboard
Side panel
Nested side panel
MCL2 (Single data grid)
MCL2 (Multiple data grids)
Adjustable Sidepanel Width (BETA)
This is a BETA release. There are open issues with this feature.
Solution Admins must decide if they want to turn on this BETA feature
Users can now expand a sidepanel’s widths.
User can drag and expand a sidepanel size up to the maximum size
The minimum size is the original size.
The sidepanel widths are saved per user session. Once a user resizes any sidepanel, the next sidepanel the user opens will be the same size.
To turn on this BETA feature, Solution Admin/Org Admin must add the following config to Org Config:
config name -
isSidePanelResizableconfig scope -
orgconfig value -
boolean, set to True
Use moment.js library in pages
Solution Admins can now use moment.js functions directly in page definitions.
Moment is now supported in web page definitions
For example, Solution Admin can configure a jslib like
CODE"checkMoment": function(pageContext) {pageContext.currentDate = moment().format('MMMM Do YYYY, h:mm:ss a');}
Moment is only supported in web page definitions and not workflows or mobile page definitions.
Advanced Search Component: Configure parent sidepanel reload
Before, the entire side panel reloads i.e. all the actions in actionOnLoad are executed when the user returns to the sidepanel after clicking save or the back button in the Advanced Search nested panel. This results in everything getting set as empty even if some values were selected before clicking on advance search, as all the initial load actions are executed again.
In this release, Solution Admins can configure if the entire parent sidepanel must reload when users return from the Advanced Search nested panel.
Solution Admin can add this key,
parentPanelRefreshRequired": falsein the advanced search component definition.If this key is false, when a user clicks on the back or save button, the parent sidepanel does not reload. Only the searchable dropdown reloads to reflect the prior advanced search selection.
Bugfixes
[ZPW-542] - Persistent XSS through Import Translation file.
[ZPW-1304] - Video Viewer Component - Troubleshoot
[ZPW-1393] - Use of lodash 4.17.15 with known vulnerabilities.
[ZPW-1395] - Use of JQuery library with known vulnerabilities.
[ZPW-1396] - Use of axios 0.17.1 with known vulnerabilities.
[ZPW-1400] - Use of "kind-of 6.0.1" library with known vulnerability.
[ZPW-1463] - MCL2 - Horizontal scroll arrows should be shown for the data grid
[ZPW-1480] - Clean up data going from Side panel forms to the API
[ZPW-1482] - Create a DOM sanitize method
[ZPW-1483] - Sanitize login form
[ZPW-1484] - Identify and Sanitize other field inputs that post data to database
[ZPW-1542] - Schedular component - The UI in the month view does not look as expected for the tasks spanning for more than 3 days
[ZPW-1544] - datetime: is24Hour is not working as expected for format m-d-Y H:m:s
[ZPW-1558] - selecting check box / radio button of the grid data is not not getting selected
[ZPW-1596] - Action on load on tab is not working properly/consistently
[ZPW-1691] - UI fixes - Sendbird Web
[ZPW-1692] - Multiple channels with same users are being created
[ZPW-1712] - UAT || NetCloud || Tab navigation arrow not working
[ZPW-1716] - Sendbird web messaging : getSendbirdProfile network call is sent for non enabled sendbird orgs
[ZPW-1722] - Blocked user has access to complete application from browser cache.
[ZPW-1740] - Side panel sticky headers - Sticky headers cover the side panel tab names
[ZPW-1744] - Japanese Localization: "Week" and "Month" to be translated
[ZPW-1749] - Avoid severe caching Zinier web app. (Login error messages should not be cached)
[ZPW-1753] - Grid Loader: loader not coming
[ZPW-1754] - Auth0 Login - UI issues
[ZPW-1778] - Auth0 - Session logout from timeout not logging out IDP
[ZPW-1779] - Auth0 - incorrect org name causing multiple getAuthType calls
[ZPW-1780] - Auth0 - 404 error ssodata call
[ZPW-1783] - Side panel Page is scrolling to the top if vertical scroll is available
[ZPW-1785] - Change error text in user activation and reset password page
[ZPW-1809] - Sendbird web messaging : Safari is not launching sendbird chat window after the push notification changes
[ZPW-1822] - DataGrid - Tool tip for the first row comes on the second row
[ZPW-1824] - Auth0: Entering https://raman.zinier.com/sign-in as url should redirect user to https://raman.zinier.com/org-id as per new implementation
[ZPW-1826] - Org Name screen: Error message is not displayed in web, when wrong org name is entered
[ZPW-1849] - Action icon not coming on hover of side-panel's grid row
[ZPW-1869] - Auth0 Login - Add Malay Localisation
[ZPW-1901] - BVConst - User Side Panel closes after saving Groups and before inviting
[ZPW-1905] - Auth0:The Z of Zinier under logo should be in small letter (UI issue)
